Safety And Security Procedures Centers (SOCs) give oversight as well as human participation to notice things the modern technologies miss, as held true in the Solar, Winds violation, where an astute partner saw something unusual and also examined. Yet also SOCs can't keep the organization 100% secure. Plans and procedures are needed to meet control needs and also those are established by management.
This does not indicate that every staff member comes to be a cybersecurity expert; it implies that each worker is held answerable for supervising as well as behaving as if he or she was a "protection champ." This includes a human layer of defense to prevent, spot, as well as report any kind of actions that can be manipulated by a destructive star.
The Ultimate Guide To Cyber Security Consulting Company
The figure has a duty in this, as well. Simply by asking questions about cybersecurity, supervisors suggest that it is a crucial topic for them, which sends out the message that it requires to be a concern for corporate execs. Right here is a list of 7 concerns to ask to ensure your board understands just how cybersecurity is being handled by your organization.
Defense is performed with several layers of defense, treatments and also plans, and various other risk monitoring techniques. Boards do not need to decide on exactly how to execute each of these layers, yet the BOD does need to recognize what layers of security remain in location, and also exactly how well each layer is safeguarding the organization.

Given that several violations are not discovered quickly after they occur, the body must ensure it recognizes just how a violation is discovered and concur with the threat level resulting from this approach. If a ransom is looked for, what is our policy concerning paying it? The board is not likely to be part of the thorough feedback plan itself, the Figure does desire to be sure that there is a plan.
Cyber Security Consulting Company - Questions
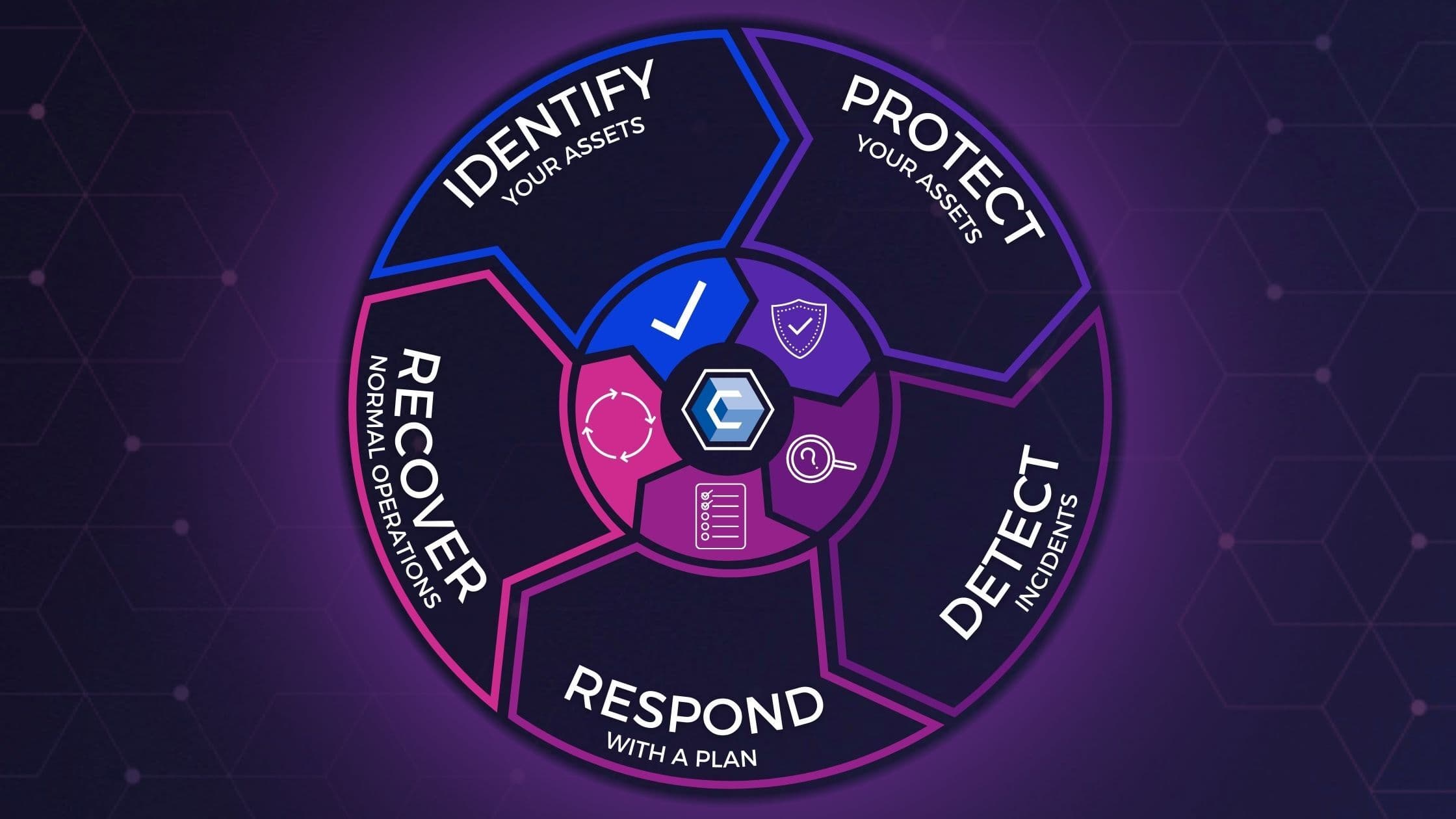
The value of Cyber safety and security has actually become evident in every facet due to the fact that all institutions have to handle their data on the net. As the globe inclines towards an electronic remodeling, where the procedures of the business, the handling, as well as several such procedures happen online, the risk of the details dripping or obtaining hacked has increased even more.
They are spending extra resources into obtaining professional team or incentivizing existing staff members to take cyber safety and security training courses so they can remain on top of the most article source recent trends. It indicates the devices, modern technologies, procedures, and also practices that are designed to keep the information risk-free from any type of kind of attack, additional info or damages, or unauthorized access.
Some Known Factual Statements About Cyber Security Consulting Company
A cyberpunk then can input malware in their system by utilizing your name. In the next decade, more people will certainly be subject to cybercrimes, these include all individuals: Who have a smart phone, That have their bank accounts, Who keep vital files as well as information on their computers, Whose name is in the straight marketing database of the firms With cybercrimes increasing at a startling rate everyday, individuals need to take sufficient procedures to shield their information or any type of crucial details they could have.
Educational systems which include the research data. With the execution of the cyber protection regulations, all this info can be shielded. The importance of cyber safety is not just to the companies or the government however little organizations as well, like the education market, the monetary organizations, and so on. Cyber safety is currently an extremely important aspect because all establishments have to update their information online.
The information can land in the wrong hands and also can become a risk to the nation (Cyber Security Consulting Company). So with the rise in the variety of cyber-attacks, the organizations, especially the ones that take care of delicate data have to take added steps to safeguard the information and also avoid the breaching of the information.
Facts About Cyber Security Consulting Company Revealed
By doing this, when you buy SSL certificate, which can be of terrific assistance as it protects the data in between the web server and also the internet browser. Cyber Security Consulting Company. Authentication and dependability are 2 structures on which SSL certificates depend on. To make sure cyber security, one read review needs to make sure that there is sychronisation in all the aspects of cyber protection.
